Consumer VPNs Are Not Tools For Businesses

Consumer VPNs Are Not Tools for Businesses If you spend any amount of time on YouTube, chances are you’ve seen videos bring up the names of various sponsors, including consumer VPNs. VPN providers take advantage of the trendiness of these influencers to spread awareness of their products. We want to make one thing […]
Managed IT Services Providers: Your Key to Streamlined Business Operations
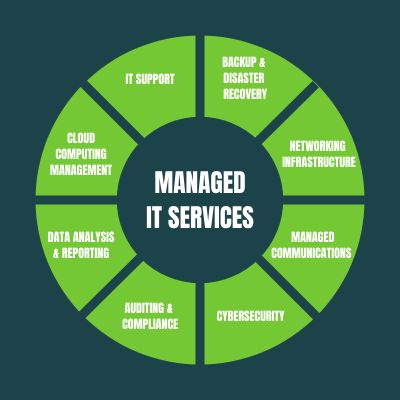
In today’s digital age, having a reliable and secure IT infrastructure is essential for success. That’s where managed services providers (MSPs) come in, offering expert support and solutions to help businesses optimize their IT operations. Today we’ll highlight the benefits of partnering with an MSP and how they can enhance your business efficiency. Streamlined […]
IT Compliance: Ensuring Security and Governance

In today’s digital landscape, where data breaches and cyber threats are on the rise, maintaining IT compliance is essential for organizations of all sizes. IT compliance encompasses a set of regulations, industry standards, and best practices that guide businesses in managing and securing their information technology systems. In this blog post, we will explore the […]
Finding a Ubiquiti Installer Near Me: Your Guide to Seamless Networking

Finding a Ubiquiti Installer Near Me: Your Guide to Seamless Networking In today’s connected world, a robust and reliable network infrastructure is essential for homes and businesses alike. Ubiquiti Networks, a leading technology company, offers innovative networking solutions designed to meet the demands of modern connectivity. If you’re looking to enhance your business networking and […]
The Power of a Virtual CIO: Driving Technology Strategy for Business Success

In today’s rapidly evolving digital landscape, businesses of all sizes face the challenge of managing complex technology ecosystems to stay competitive. While larger organizations often have the resources to hire a dedicated Chief Information Officer (CIO), smaller and mid-sized businesses can benefit from the expertise of a Virtual CIO. In this blog post, […]
Enhancing Business Efficiency and Innovation through Technology Consulting

In today’s rapidly evolving business landscape, technology has become the driving force behind growth and success. Whereas technology used to be one area of an organization, it is now the building block on which an entire company is run. Operations, management, finance, sales and marketing, and even R&D all rely on technology. As organizations strive […]
Maximize Profitability with Managed Services

Maximize Profitability with Managed Services Your business relies on its profits and continued profitability to succeed, but this priority is surprisingly challenging. By investing in a managed service provider, however, you can gain a considerable advantage while improving your productivity, thus resulting in increased profits for your business. Let’s look at how a managed […]
Ransomware Remediation: Safeguarding Digital Landscapes Against Cyber Extortion

Ransomware is a major threat in today’s digital age, when technology has become a part of our everyday lives. Ransomware has become more sophisticated and common, posing a significant threat to businesses, individuals and governments. This article will explore the world of ransomware, and the strategies, best practice, and emerging trends which can help businesses […]
Why IT Compliance is Essential

IT compliance refers to adhering to rules, regulations, and standards governing the use of information technology within an organization. These may come from government agencies, industry organizations or internal policies and it is vital that an organization operates within legal and ethical boundaries while safeguarding sensitive customer data and maintaining customer trust. Why Is IT […]
Your Password Can Probably be Cracked Faster Than You’d Think

Your Password Can Probably be Cracked Faster Than You’d Think Whether you’re talking about identity theft, data breaches, or any other form of cybercrime, one of the leading causes of successful cyberattacks is the use of insufficiently secure passwords. Just how easy is it for someone to bypass such a password? […]


