When Microsoft Stops Supporting Windows
When Microsoft Stops Supporting Windows Microsoft only supports each version of Windows for a certain period and the end of its support for a software product can be a significant challenge for businesses. Currently, Windows 7 is on “extended support” until January 14, 2020. What does it mean when Microsoft terminates support of your Windows […]
5 Cloud Security Tips for Business Owners
5 Cloud Security Tips for Business Owners Cloud computing marketing can be deceiving. When you see an image of the cloud, it’s often a happy, bubbly, white puffball floating delightfully in front of a blue sky background. Its presence is both calming and reassuring, which makes you believe that anything is possible. Security would never […]
The End is Near. Windows 7 End of Life.

The End is Near. Windows 7 End of Life. When Microsoft stops supporting Windows Microsoft only supports each version of Window for a certain period and the end of its support for a software product can be a significant challenge for businesses. Currently, Windows 7 is on “extended support” until January 14, 2020. Consequently, you […]
Cutting Corners and Disingenuousness

Cutting Corners and Disingenuousness Do you want to work with a company that cuts corners? Does the fact that they cut corners with their public persona make you wonder how they’ll handle your company? Or is it something that can be overlooked? I come from a competitive intelligence and market analysis background, so I like […]
An Ounce of Prevention?

An Ounce of Prevention? My absolute, without a doubt, least favorite part of my role as sales and marketing manager for Ashton Technology Solutions is the cold calling. Fortunately, our other sales guy Pete is old school and seems to love it. He comes in every morning and makes 20-30 phone calls, then spends the […]
Cyber Criminals Target Wire Transfers

Cyber Criminals Target Wire Transfers Do you or a client work in an industry where wire transfers are common? Think real estate (commercial or residential), law, finance, architecture, construction, or manufacturing, to name a few. If you do, you need to take care EVERY time you are involved in (either sending or receiving) a money […]
Cleaning Up a Server Room Mess

Cleaning Up a Server Room Mess If you’ve ever been in the server closet at your place of work, chances are you’ve seen a tangled mess of cables connecting switches, patch panels, firewalls, and servers. If you’re in the least bit OCD or a neat-freak, it probably drives you nuts. And not only is it […]
Phishing for Gift Cards

Phishing for Gift Cards Yesterday, the email shown below was sent to Ashton’s “security alert” distribution list. The topic is the recent spate of email spoofs asking that an employee send iTunes gift cards to a company exec, so they can be given to clients. In the 24 hours since the email was sent, we’ve […]
Takeaways from #NotPetya

Takeaways from #NotPetya It’s been over a year since the NotPetya ransomware made it’s way around the world, with a primary focus on Europe. Since that time, the companies who were directly effected (those whose networks were shutdown and were unable to do business) have faced costs of well over $1B. That doesn’t include the […]
Temporary Wireless Network Installation
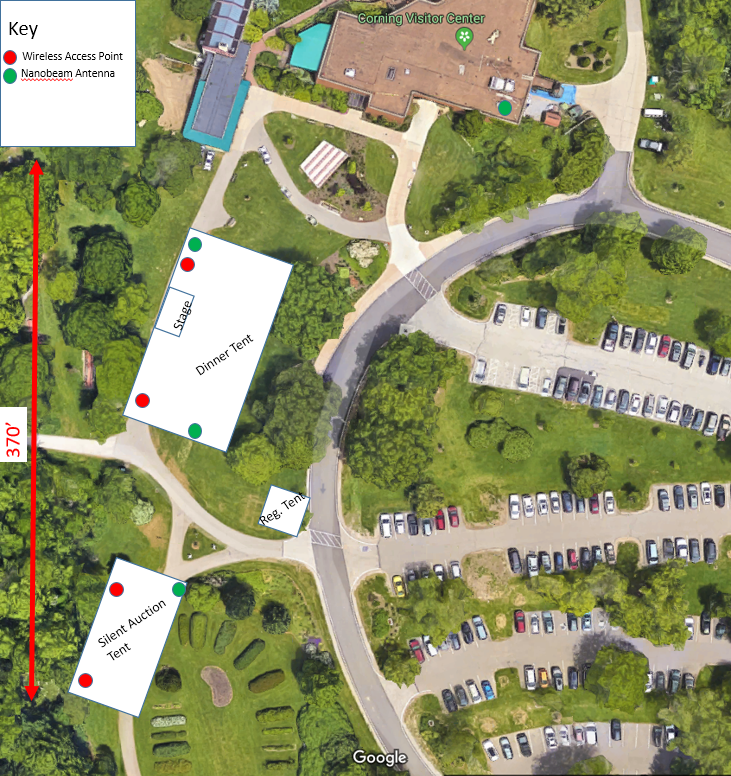
Temporary Wireless Network Installation Ashton was recently approached by Holden Forests and Gardens to create a temporary private wireless network for the Holden Arboretum’s annual Woodland Twilight Benefit. This benefit typically attracts 400-500 attendees, and is the organization’s largest benefit of the year. While the space itself is not overly large, and the installation not […]


