4 Resolutions to Keep Your Business Secure in 2018

4 Resolutions to Keep Your Business Secure in 2018 With every new year comes great new opportunities, and 2018 is no different. However, change can be a good thing, and with a new year also comes more perspective and knowledge that you can use to make considerable improvements to the way you run your organization. […]
Tip of the Week: Don’t Let Your Old Android Device go to Waste

Tip of the Week: Don’t Let Your Old Android Device go to Waste Unless you’re the trade-in or hand-me-down kind of person, it’s likely that you have a supply of old Android devices squirrelled away somewhere. You know, just in case the one who have now breaks. However, these old devices can be useful in […]
2018 is Expected to See $96 Billion in IT Security Investments

2018 is Expected to See $96 Billion in IT Security Investments If you were considering increasing your investment into your information security in 2018, you certainly aren’t alone. Gartner released a report that indicated a considerable rise in plans to invest in key security considerations. Closer analysis of these considerations shows that businesses around the […]
Tip of the Week: Never Pay to Print Business Cards Again

Tip of the Week: Never Pay to Print Business Cards Again It’s just good business to hand out your business card to prospective clients, and it has been for a very long time. As far back as the Renaissance, special guests were announced with name cards that displayed who the guest was and what types […]
ALERT: Your Business’ Infrastructure May Be Susceptible to Meltdown/Spectre Vulnerability
ALERT: Your Business’ Infrastructure May Be Susceptible to Meltdown/Spectre Vulnerability You’d think that Intel would make sure their firmware is of sound integrity, but unfortunately, a recently discovered vulnerability has revealed that it’s not as secure as previously thought. The issue involving Intel’s chips could potentially lead to a permanent nosedive for your CPU’s capacity […]
20-Year-Old Exploit Finds New Life as ROBOT

20-Year-Old Exploit Finds New Life as ROBOT There is no shortage of threats on the Internet, from situational issues to deliberate attacks meant to damage your company or steal your valuable data. While new threats pop up almost every day, some have been around for some time–so long, that many seem to not consider them […]
Scam Leverages Email from a Reluctant Contract Killer

Scam Leverages Email from a Reluctant Contract Killer To many, email scams have become a joke. Sitcoms have throwaway punchlines that reference a character getting an email from a rich uncle in Nigeria, or some friend needing funds to get home from an overseas trip. One of these scams may not at first seem to […]
Proper Hard Drive Disposal is An Involved Process
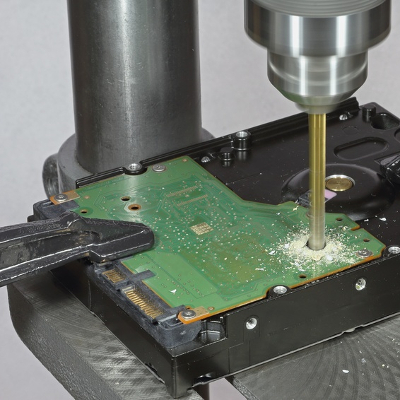
Proper Hard Drive Disposal is An Involved Process When a business utilizes any kind of technology, there will come a time when that technology needs to be replaced–which means that the business will need to be sure that any data on the old machines cannot be recovered. This, in turn, means that the machine’s hard […]
Tip of the Week: Why You Should Reconsider Your Best Practices

Tip of the Week: Why You Should Reconsider Your Best Practices The term “best practice” has been used by businesses for years to describe the optimal way of performing a particular task. However, before fully adopting them into business operations, it is important for these practices to be examined and deemed to be beneficial to […]
Which is More Secure, Your Mobile Network or Wi-Fi?

Which is More Secure, Your Mobile Network or Wi-Fi? For the modern business, having a strategy to manage your employees smartphone use is essential. This is because most of the people that work for you have smartphones. One study shows that upwards of 90 percent of people under 30 own a smartphone. If you have […]


