Can Your Bed Keep A Secret?

Can Your Bed Keep A Secret? Maybe your first question is (and probably should be): What secret could my bed have and who would it tell anyway? If you have any familiarity with the Sleep Number bed you may also have heard of the Sleep IQ option that you can get. I had not previously […]
The Cat’s in the Cradle, the RAT’s in the Server
The Cat’s in the Cradle, the RAT’s in the Server Observations from the banks of the technology river TOM EVANS; ASHTON ENGINEER EMERITUS Some mail arrived just the other day Landed In my inbox with a lot to say But there were others to read and not much time I clicked on the link and […]
Security Costs Too Much for Manufacturers

Security Costs Too Much for Manufacturers Fatal Attraction (1) As CTO (Chief Technology Officer) for MegaTech, Fred was used to getting tech gadgets in the mail. It was a perk of the position and he loved tech gadgets. Sometimes they were pitiful, sometimes interesting, some were wildly impractical. Most of the time they were not […]
Have You Set Yourself Up for Account Takeover (ATO)?
Have You Set Yourself Up for Account Takeover (ATO)? Facebook, Google, loyalty points and Account Take Over (ATO) A report published by Forter (fraud prevention) raises concerns around how intertwined social and commercial aspects of web usage have become. It also indirectly highlights just how much can be determined about us based on what we […]
10 Billion Records and Deepfakes
10 Billion Records and Deepfakes Now that 2018 is history, I decided to see what happened last year in the way of data breaches. A lot of press covered ransomware and cryptomining, while breaches faded into the background–like how a really loud noise that doesn’t stop eventually fades from perception. Since it seems to be […]
Secrets
Secrets If you watch crime dramas or mysteries, you have seen numerous episodes where blackmail plays a part. The victim has done something that they don’t want to become public knowledge, and revealing the misdeed will have serious consequences. Hence the demand for money in order to maintain silence. On TV, the blackmailer never stops […]
Let’s Go Shopping; How ’bout The Dark Web?
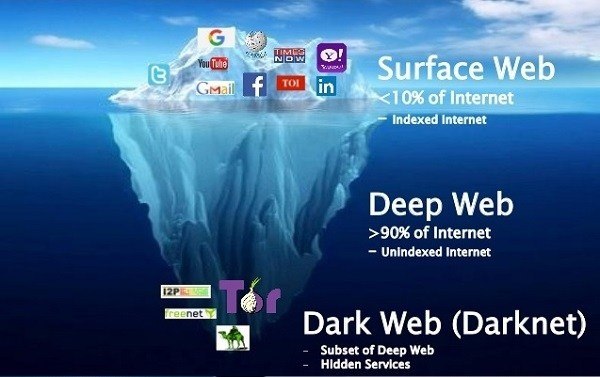
Let’s Go Shopping; How ’bout The Dark Web? If you were to go shopping online but elected to bypass Amazon for the seedier parts of the Internet you might find ads that look like the following; For Rent : ATTACK YOUR ENEMIES or anyone. Do you have someone you want to knock off the ‘net? […]
SMS, GPS, and Your Favorite Movie.

SMS, GPS, and Your Favorite Movie. I have several sites that I get RSS feeds from, and as you might expect, many of them relate to security. Consequently, I see headlines that run the gamut from discussing sophisticated attacks on the computer CPU (Spectre, Meltdown, etc), to phishing attacks, to poor security in IoT devices. […]
Hurricanes and Cybersecurity
Hurricanes and Cybersecurity So I have been ‘retired’ for about 3 ½ years now but I keep my hand in security by doing security awareness training for Ashton. Since this encompasses some clients who understand the value of training and others who don’t, I am always on the lookout for new training material and situations […]
Plant Your Flag Online

Plant Your Flag Online NMK, PYF, IoT (again) Sometimes as I read various news feeds and articles on the state of security, or lack thereof, I start to listen to that not so faint Luddite voice saying “GET OFF THE ‘NET. It’s not safe out there. Bad people are out to get you”. Data breaches, […]


