
Be Proactive with Your Technology to Prevent Problems Altogether
If your business could go about its daily tasks without having to worry about technology, you would find yourself suddenly much more productive and efficient.

Ashton Solutions Ranked on Channel Futures 2023 MSP 501
Tech Industry’s Most Prestigious List of Managed Service Providers Worldwide Annual MSP 501 Identifies Industry’s Best-in-Class Businesses Growing Via Recurring Revenue and Innovation

IT Support for Non-Profits
In today’s digital age, non-profit organizations are increasingly reliant on technology to streamline their operations, engage with stakeholders, and maximize their impact. However, managing

Consumer VPNs Are Not Tools For Businesses
Consumer VPNs Are Not Tools for Businesses If you spend any amount of time on YouTube, chances are you’ve seen videos bring up
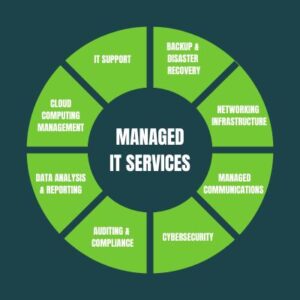
Managed IT Services Providers: Your Key to Streamlined Business Operations
In today’s digital age, having a reliable and secure IT infrastructure is essential for success. That’s where managed services providers (MSPs) come in, offering expert

IT Compliance: Ensuring Security and Governance
In today’s digital landscape, where data breaches and cyber threats are on the rise, maintaining IT compliance is essential for organizations of all sizes. IT

Finding a Ubiquiti Installer Near Me: Your Guide to Seamless Networking
Finding a Ubiquiti Installer Near Me: Your Guide to Seamless Networking In today’s connected world, a robust and reliable network infrastructure is essential for homes

The Power of a Virtual CIO: Driving Technology Strategy for Business Success
In today’s rapidly evolving digital landscape, businesses of all sizes face the challenge of managing complex technology ecosystems to stay competitive. While larger
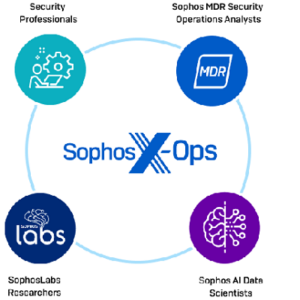
Choosing the Right Managed Detection and Response Vendor: Safeguarding Your Business from Advanced Threats
In today’s complex cybersecurity landscape, organizations face the daunting challenge of defending against sophisticated cyber threats. Managed detection and response (MDR) has emerged as
