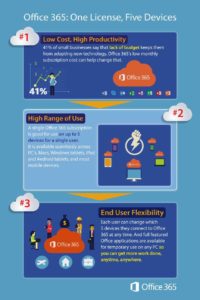
Microsoft Licensing; One License, Five Devices
Microsoft Licensing; One License, Five Devices Much to the dismay of some, one Microsoft license can’t be shared amongst five users. Instead, that one license

Data Loss Can (and Will!) Affect Your Entire Business
Data Loss Can (and Will!) Affect Your Entire Business Data loss, on any scale, is an organizational nightmare. Not only do you have to restore

How Can Office 365 Help a School?
How Can Office 365 Help a School? This week, Ashton Technology Solutions looks at how Microsoft Office 365 helps the teachers at Broadclyst School gain
Tech Term: What is a Dongle?
Tech Term: What is a Dongle? There are countless examples of words that have evolved to meet the needs of their times. Meat once referred

Secure Data Storage with OneDrive for Business
Secure Data Storage with OneDrive for Business Ashton Technology Solutions loves this new short clip from Microsoft. It highlights the incredible amount of secure data

Have You Considered What You’re Really Losing When You Lose Your Phone?
Have You Considered What You’re Really Losing When You Lose Your Phone? Losing a smartphone can be a problem for anyone. For the modern business,

Encrypt and Protect Your Data with a VPN
Encrypt and Protect Your Data with a VPN If you’ve ever felt as though someone was watching what you were doing while you were working

Tech Term: HTML vs Plain Text
Tech Term: HTML vs Plain Text As a business owner, we’re sure that you’ve spent some time around computers. You might have even seen the

Email Malware is the New Schrödinger’s Cat
Email Malware is the New Schrödinger’s Cat There is a famous thought experiment devised by physicist Erwin Schrödinger, describing a very particular paradox in quantum


